Red Team Pen Testing
Test the strength of your physical and cyber defences with Red Teaming.
Social engineering causes 98% of attacks.
Expert red team security testing
In-depth assessments to test your detection and response capabilities.
Simulated attack
Red teaming tests how an organization would handle a targeted attack.
Trusted provider
Our certified ethical hackers will conduct your test with minimal disruption to your operations.
Comprehensive tests
A multi-layered approach tests people, processes and physical premises through adversary modelling.
Prevent breaches
Get a detailed report with practical solutions to address problems before they become vulnerable to exploitation.
Red teaming vs pen testing
Penetration testing traditionally involves the identification and exploitation of as many vulnerabilities as possible within a limited timeframe. Red team testing, on the other hand, is a much more comprehensive process that evaluates your organization’s ability to withstand a targeted attack.
By engaging the services of TMBS for a red team test, you will be able to get the following objectives:
- Evaluate your capability to detect and respond to threats
- Unearth weaknesses in your organization’s human, physical, and cybersecurity defences
- Establish priorities for security risks based on their criticality
- Determine whether your organization can endure a genuine attack
- Demonstrate the effectiveness of your current security investments while also identifying areas that require further attention.
Following your red team test, you will receive a comprehensive report that outlines all security concerns. This report will assist you in fortifying your defences and avoiding actual breaches.
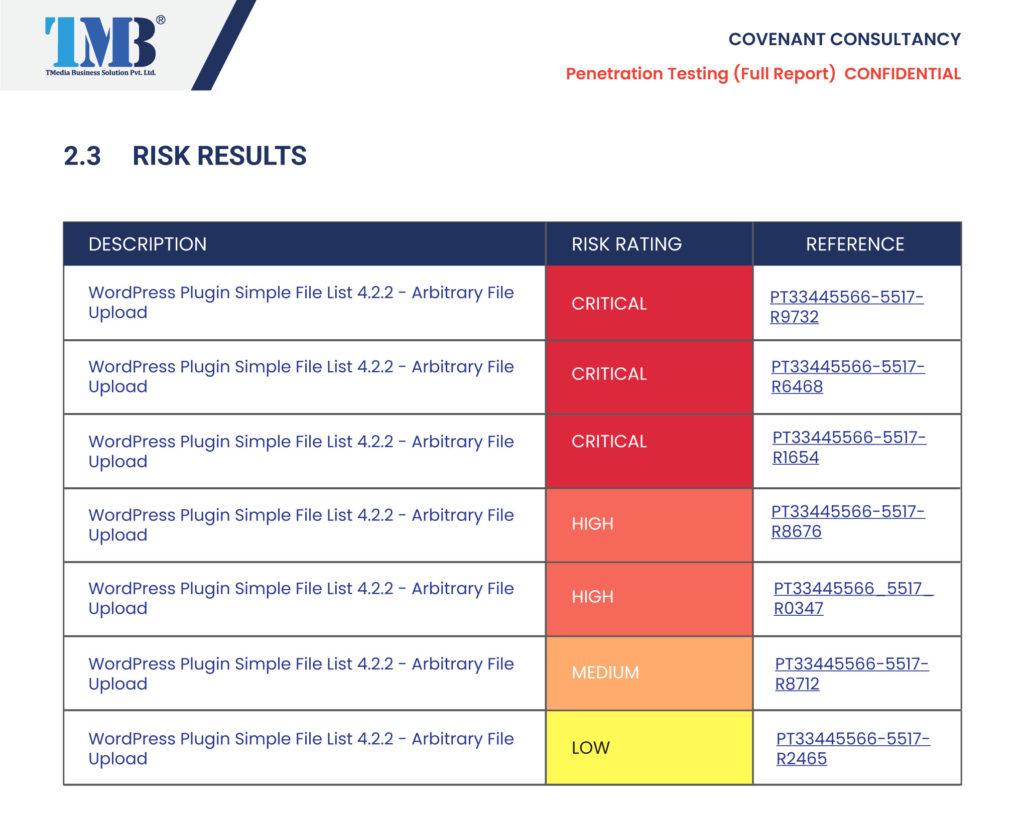
Comprehensive reporting
In the event that you engage TMBS for a red team test, you will receive a comprehensive report that will be securely hosted on our web platform. This report will contain a meticulous breakdown of every issue discovered during the test, accompanied by detailed remediation guidance.
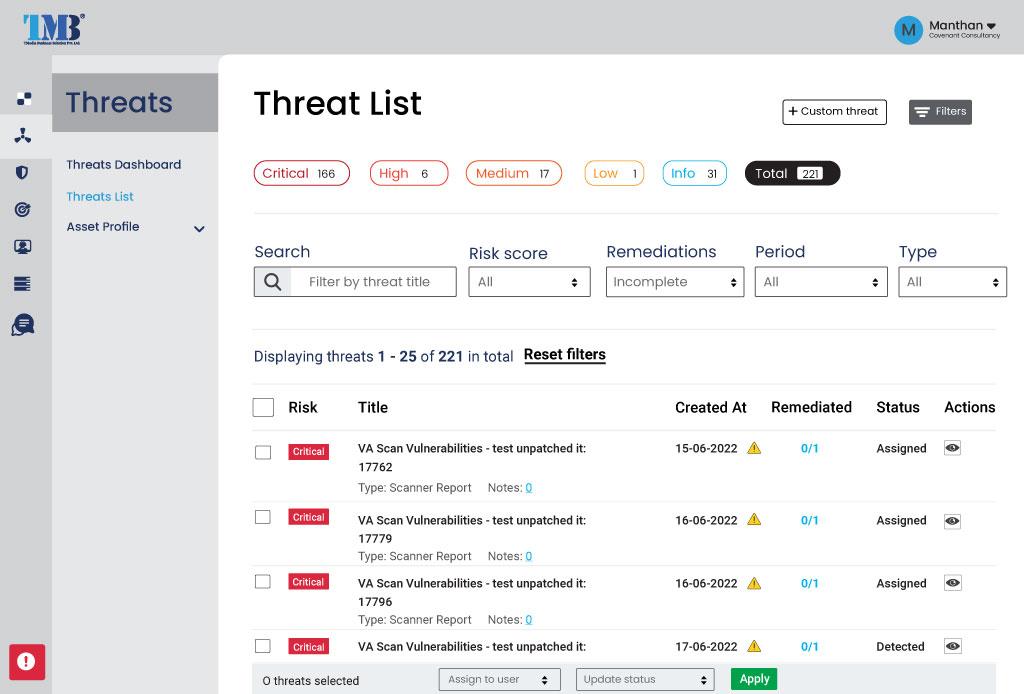
Moreover, in addition to the PDF report, our proprietary platform, TMBS, offers a user-friendly interface that facilitates the swift identification, prioritization, and management of each threat. This feature saves you both time and resources while also ensuring that your organization is well-equipped to address and mitigate any security risks that may arise.
Get more than just a red team test
Your red team assessment, will not only receive a comprehensive report but also gain 12-months access to the TMBS platform. This includes an array of useful tools such as:
- Threat management tools designed to assist you in addressing and mitigating the issues discovered during your test
- Vulnerability scanning for up to five IP addresses, enhancing your overall security posture
- External attack surface monitoring, providing you with an attacker’s perspective of your business
Alternatively, you may opt for the TMBS Enterprise package, which offers an expanded range of features. Please do not hesitate to contact us for more information and a customized quote.

Our penetration testing team
We prioritize building the best cyber talent to ensure our services remain at the forefront of the ever-changing threat landscape. Our team of 20+ experienced and certified penetration testers deliver a wide range of tests to industry standards.
Red team testing methodology
Our proficient specialists follow a defined methodology to assess your security perimeter and incident response plan.
Scope definition
We will collaborate with you to establish customized objectives and constraints for your red team engagement, aligned with your business goals.
Intelligence gathering
Our proficient professionals employ sophisticated methodologies, cutting-edge OSINT tools, and social engineering tactics to amass critical intelligence that can aid in infiltrating the target. Depending on the extent of the test, this may encompass scrutinizing your physical facilities, staff, networks, and cyber defence mechanisms.
Exploitation
Employing an array of tailored exploits and pre-existing software, our proficient penetration testers will scrutinize your system and capitalize on all detected vulnerabilities.
Physical access intrusion
Utilizing the obtained data, our testers will endeavour to attain physical entry into your target premises within the predetermined parameters of the test scope.
Post-exploitation
Our team will assess the potential risks and adapt to other networks and domains, if relevant to the scope of the exercise. All contaminated systems will be meticulously sanitized of any malware.
Reporting
Upon completion of the security testing, our team will furnish you with an all-inclusive report detailing their discoveries, and you may request additional information or clarification on critical aspects of the assessment.
Contact us with any questions.
(079) 48929022
+1 (908) 334-4476
Stay Connected
Locate Us

USA
12, French Meadow Ln, Rochester NY 14618, USA.

INDIA
Ratnakar Nine Square, Ahmedabad, INDIA

CANADA
66, Westhampton Drive, Vaughan, Ontario, Canada.

BELIZE
Belize City, Belize